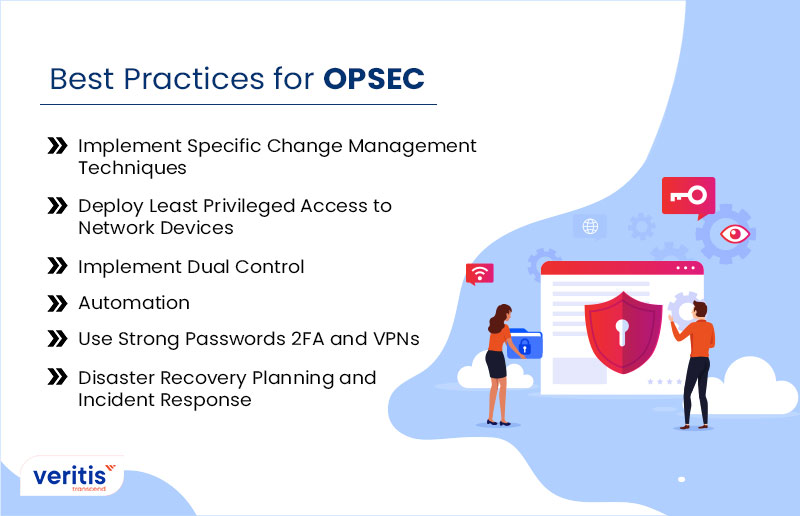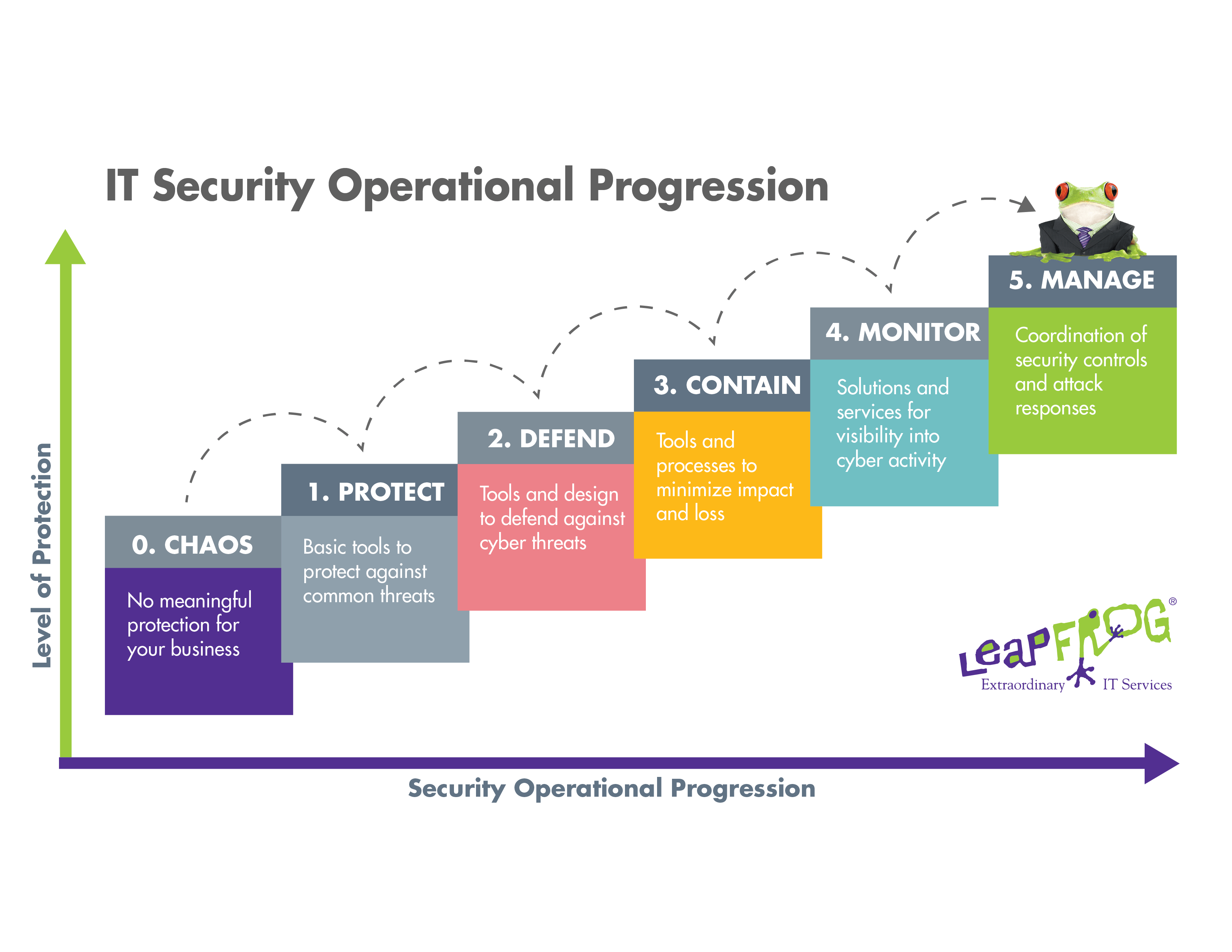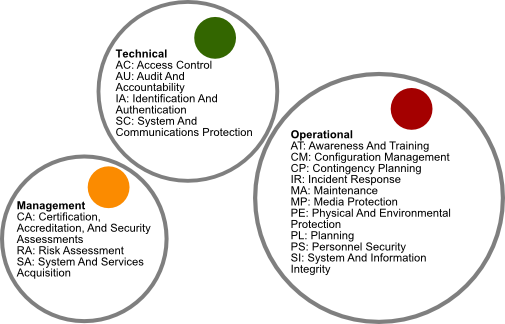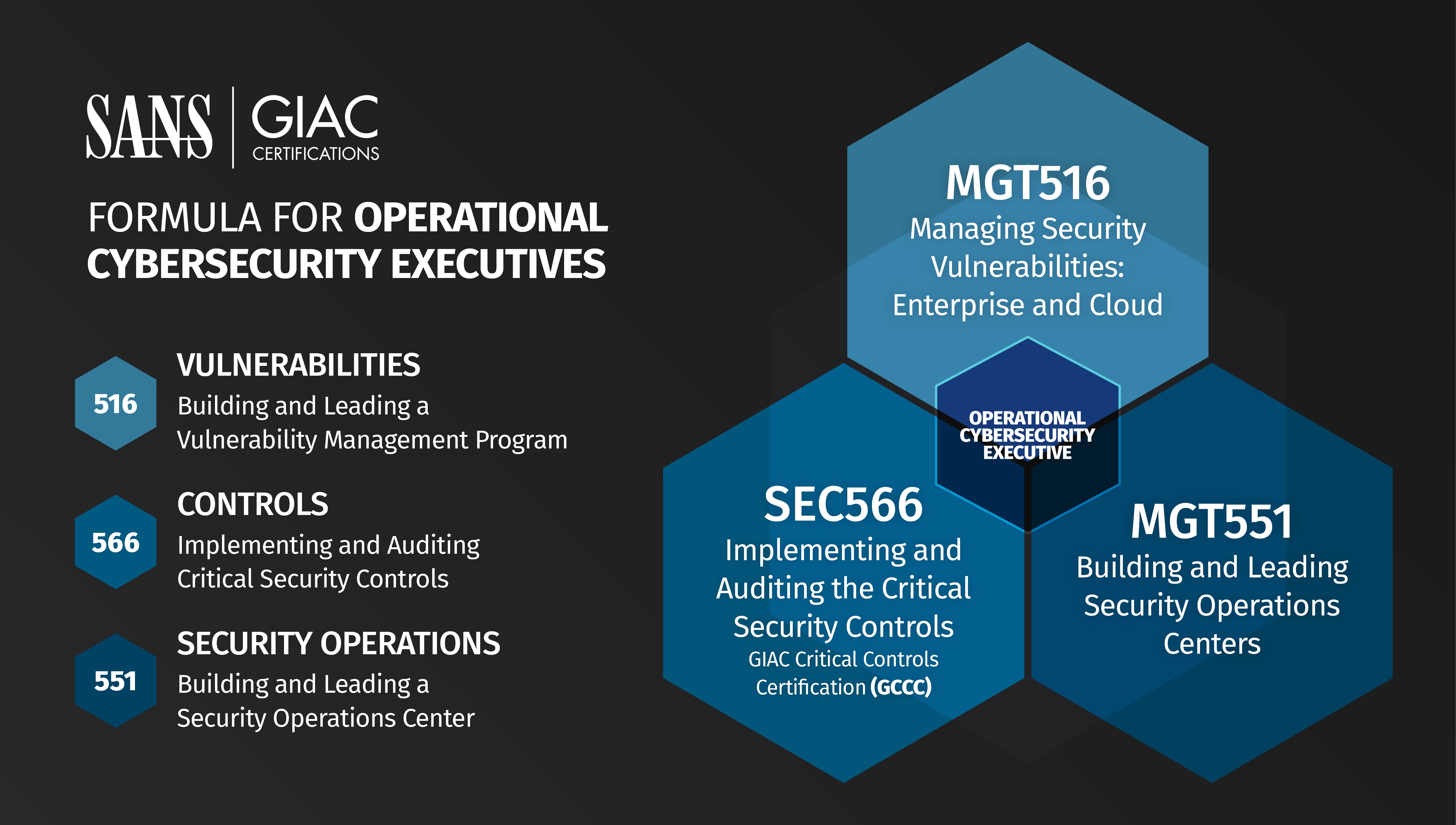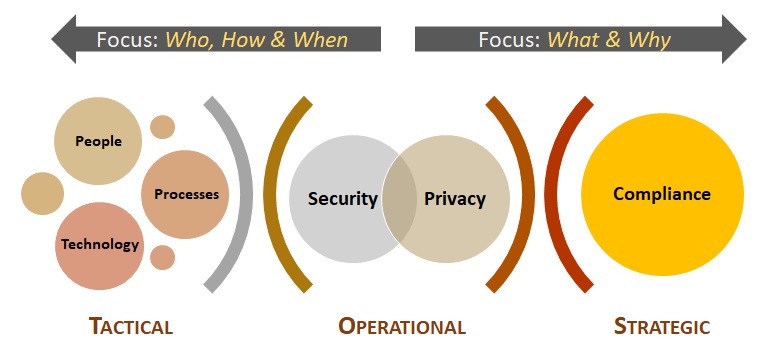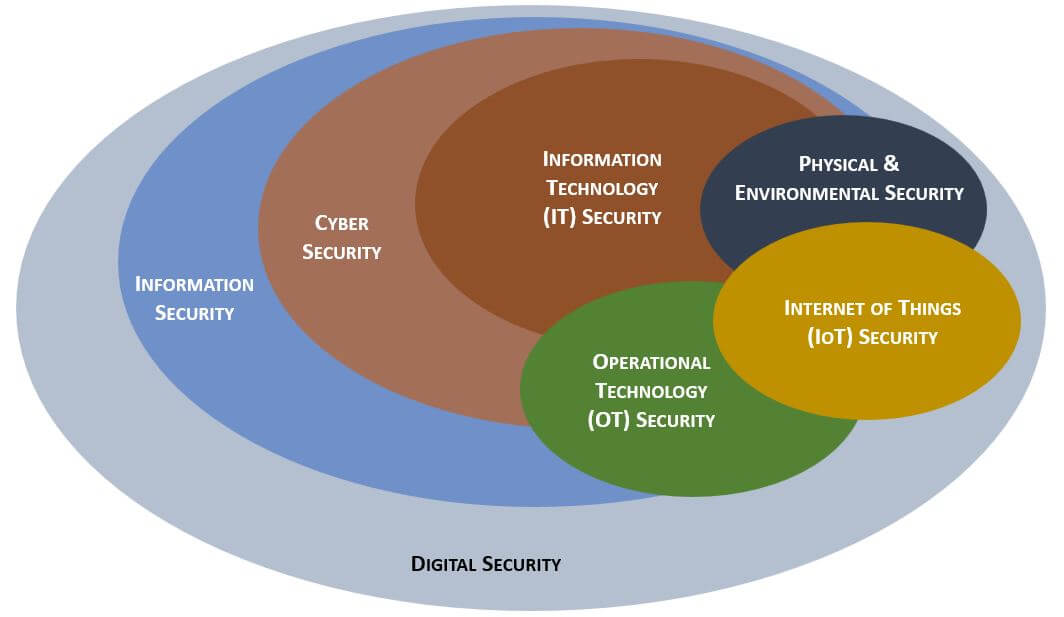
Reasons To Buy - Alignment With Secure Practices - Secure Controls Framework (SCF) - ComplianceForge
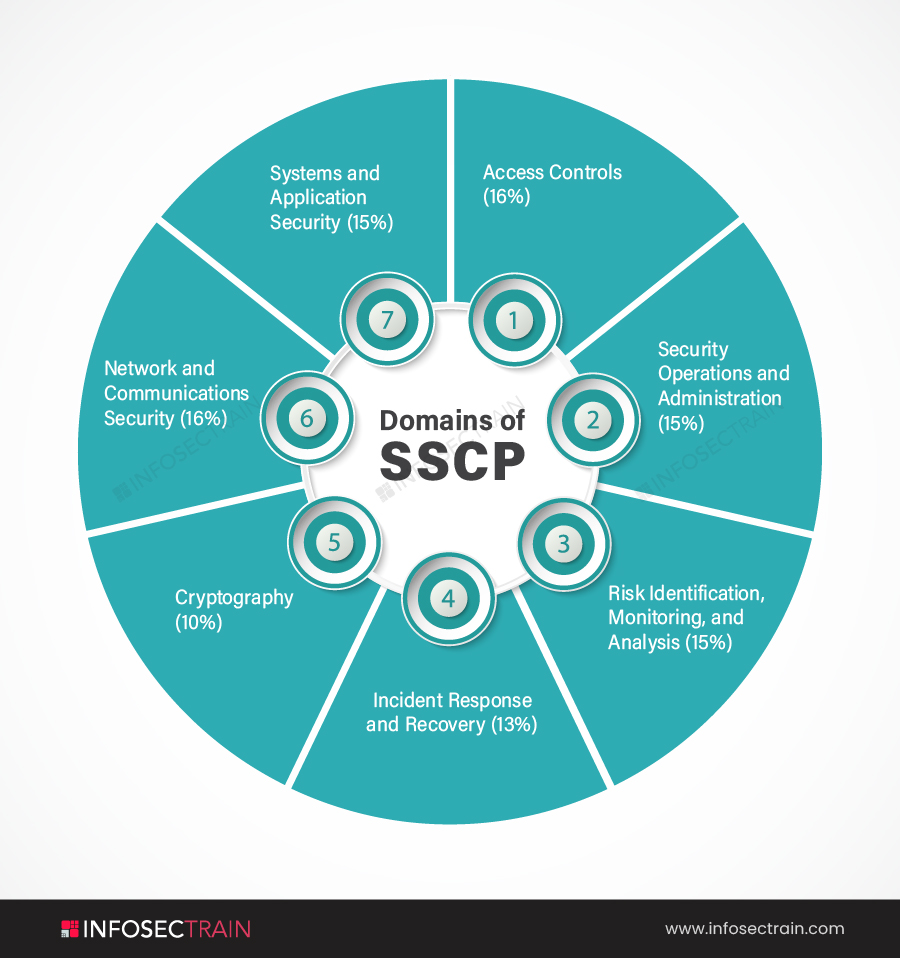
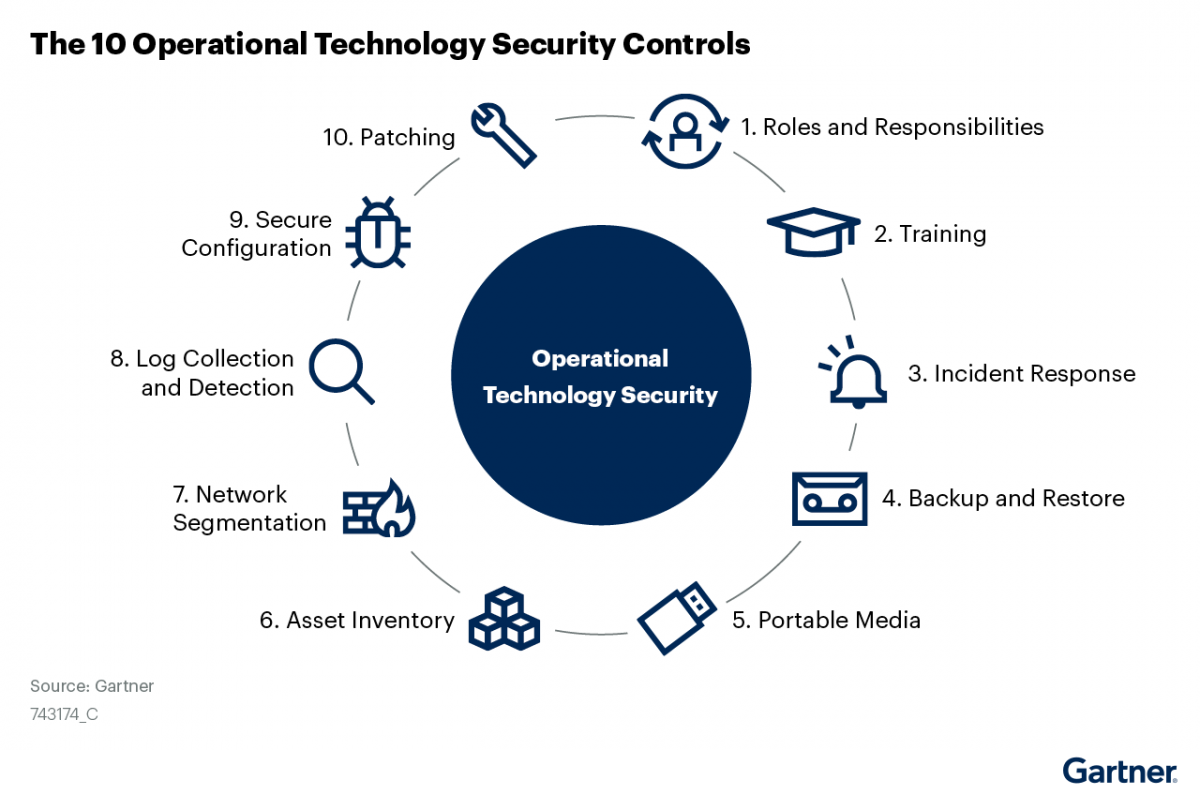
Exploring SSCP Domain 2: Security Operations and Administration for a Career in IT Security - InfosecTrain
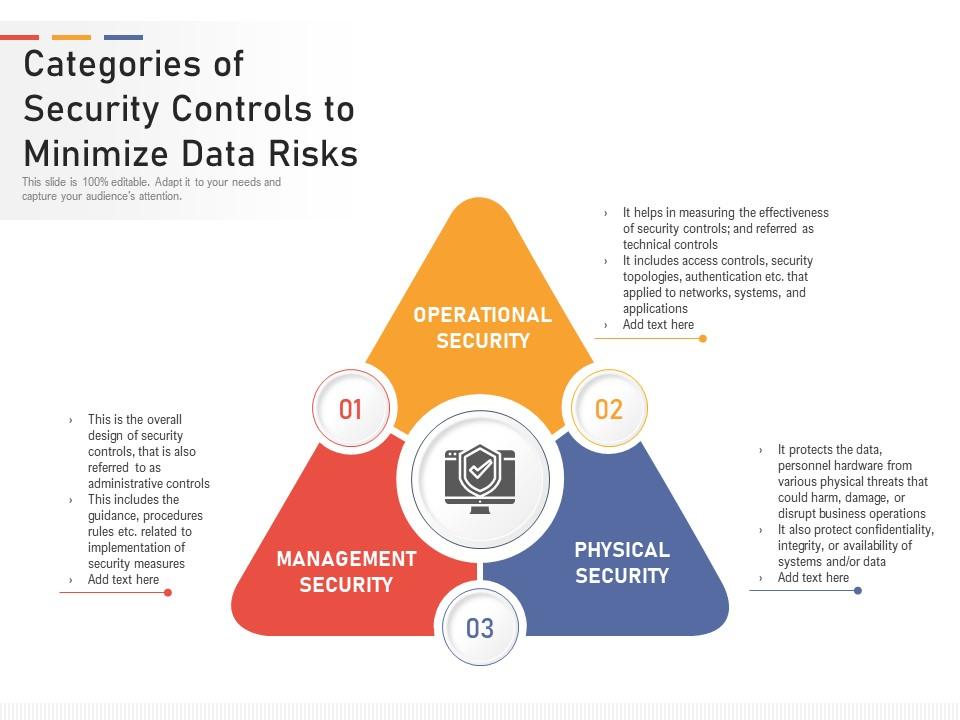
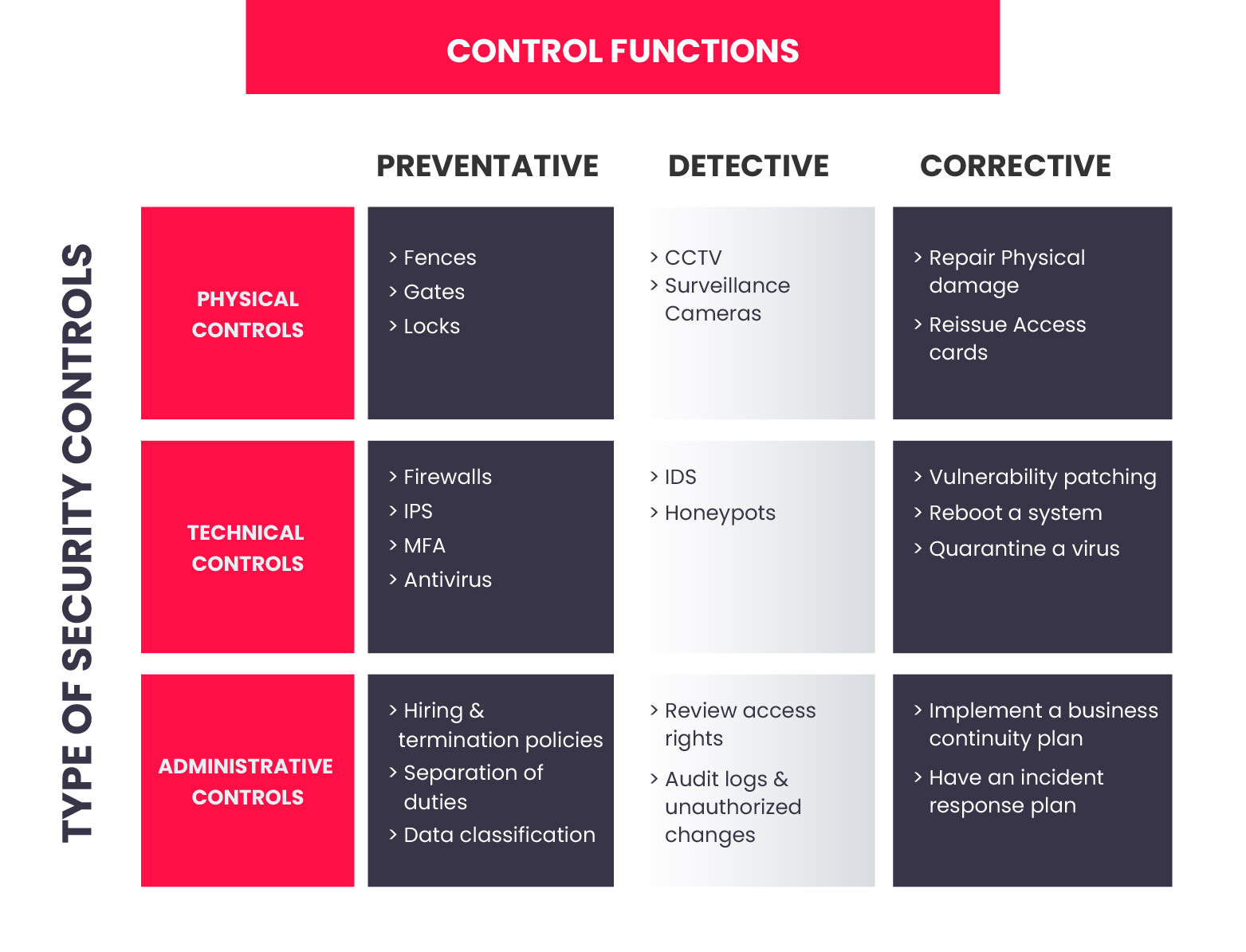
Categories Of Security Controls To Minimize Data Risks | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
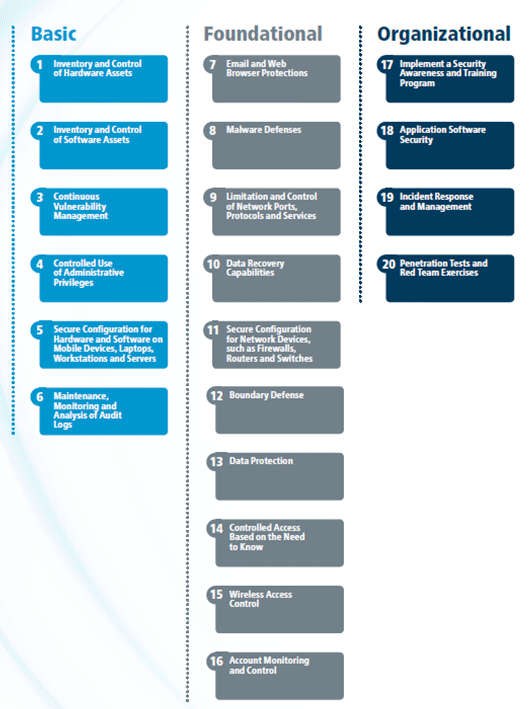
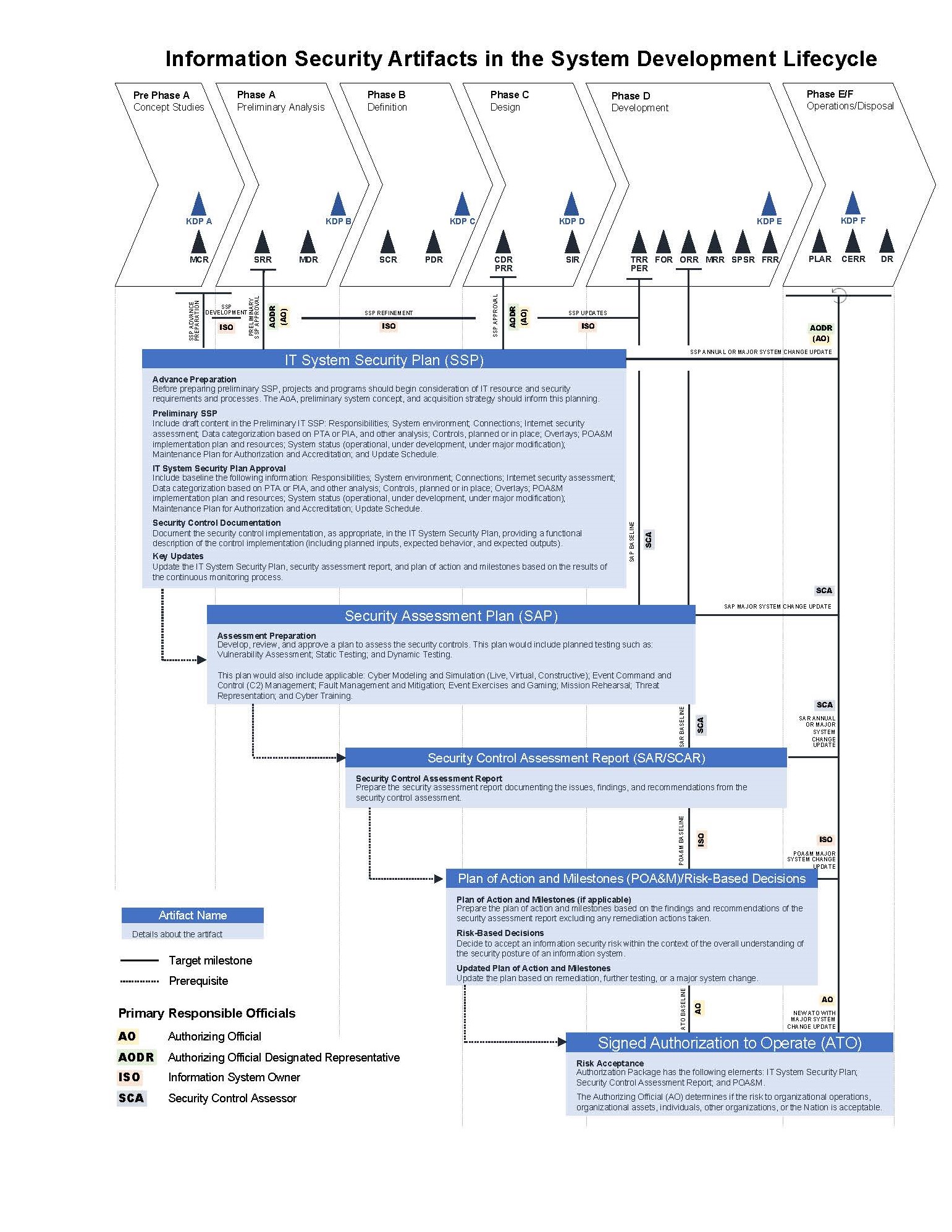
Transportation Management Center Information Technology Security - Chapter 3. Best Practices for Traffic Management Centers Information Technology Security - FHWA Office of Operations
![Comparing the Classes of Controls - SSCP Systems Security Certified Practitioner All-in-One Exam Guide [Book] Comparing the Classes of Controls - SSCP Systems Security Certified Practitioner All-in-One Exam Guide [Book]](https://www.oreilly.com/api/v2/epubs/9780071771566/files/f0255-01.jpg)
Comparing the Classes of Controls - SSCP Systems Security Certified Practitioner All-in-One Exam Guide [Book]