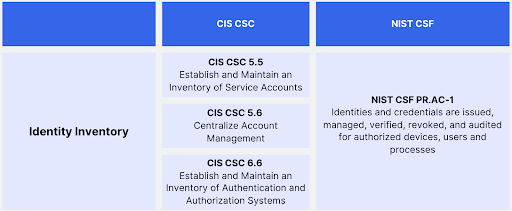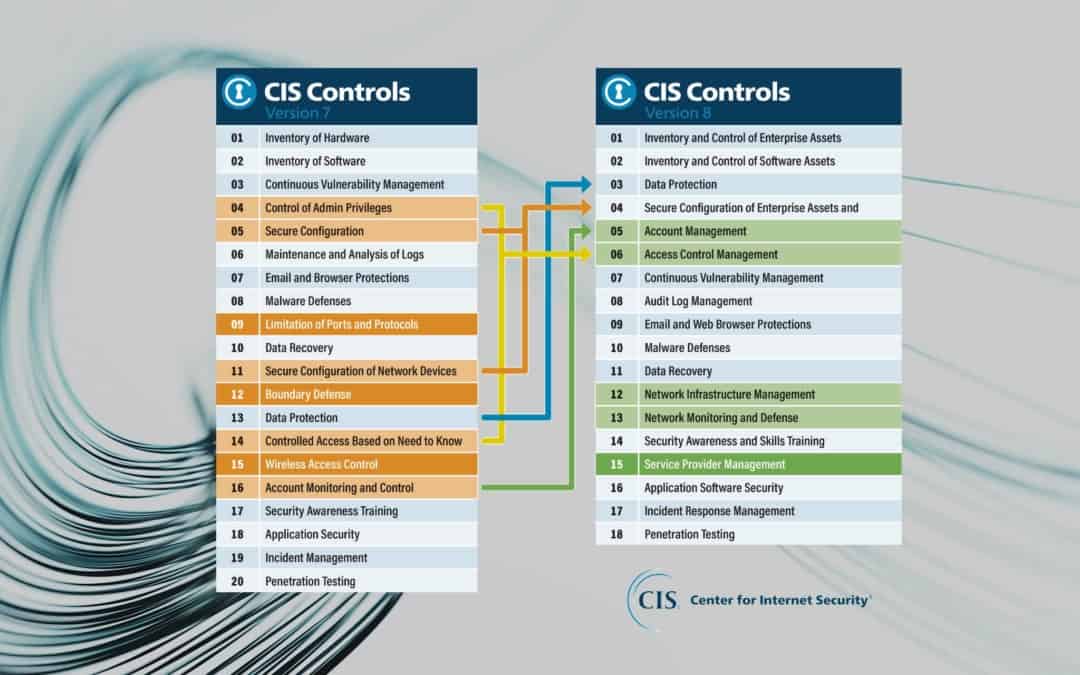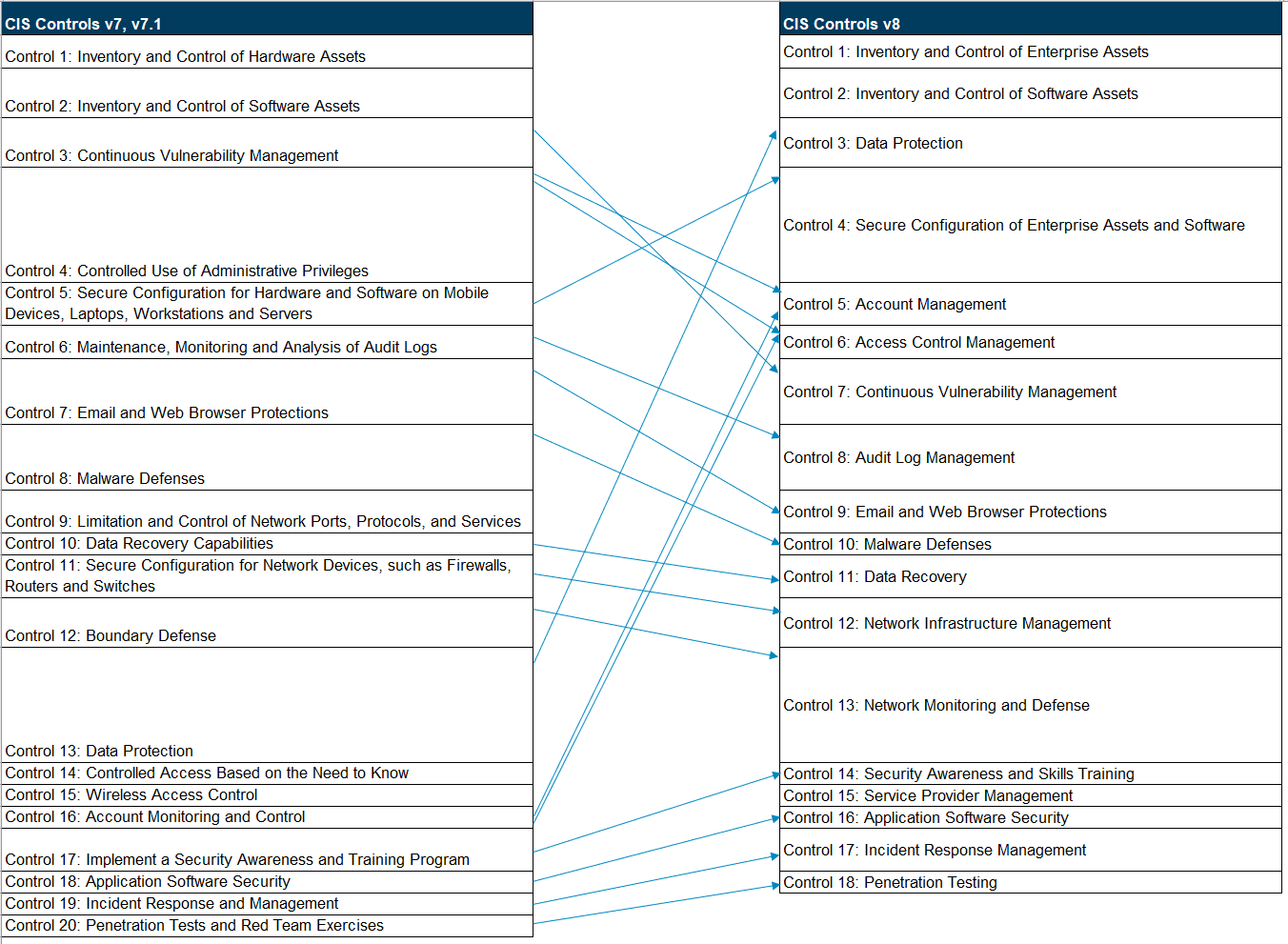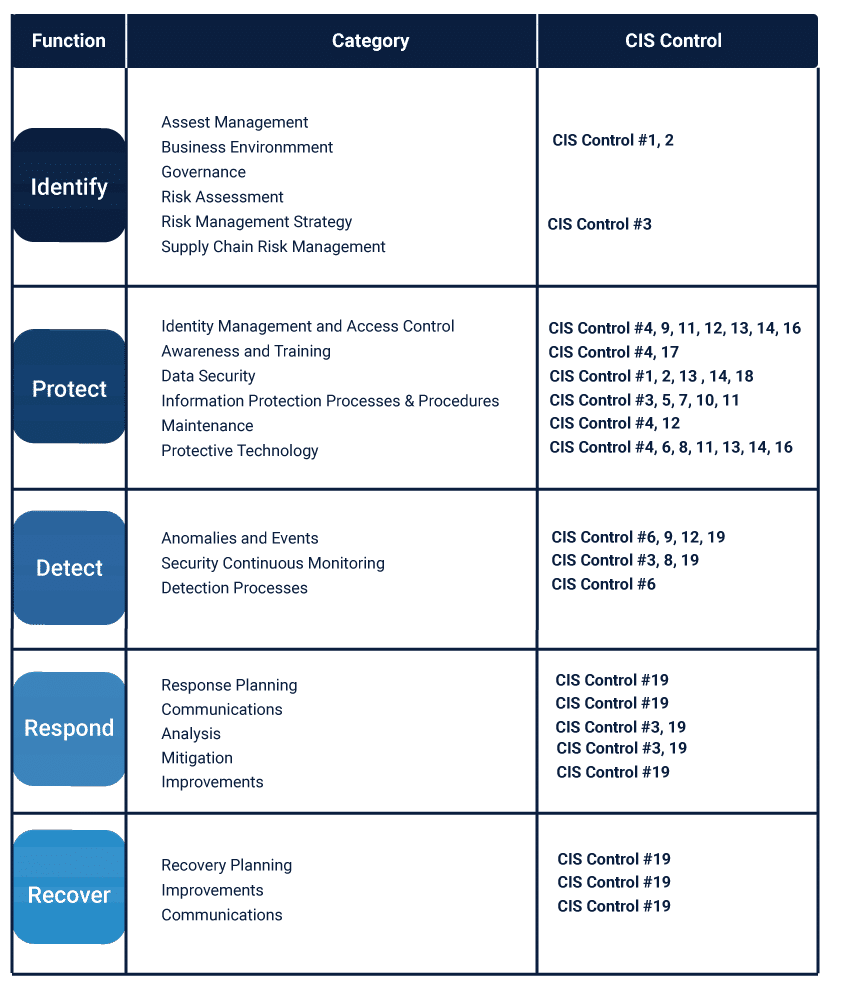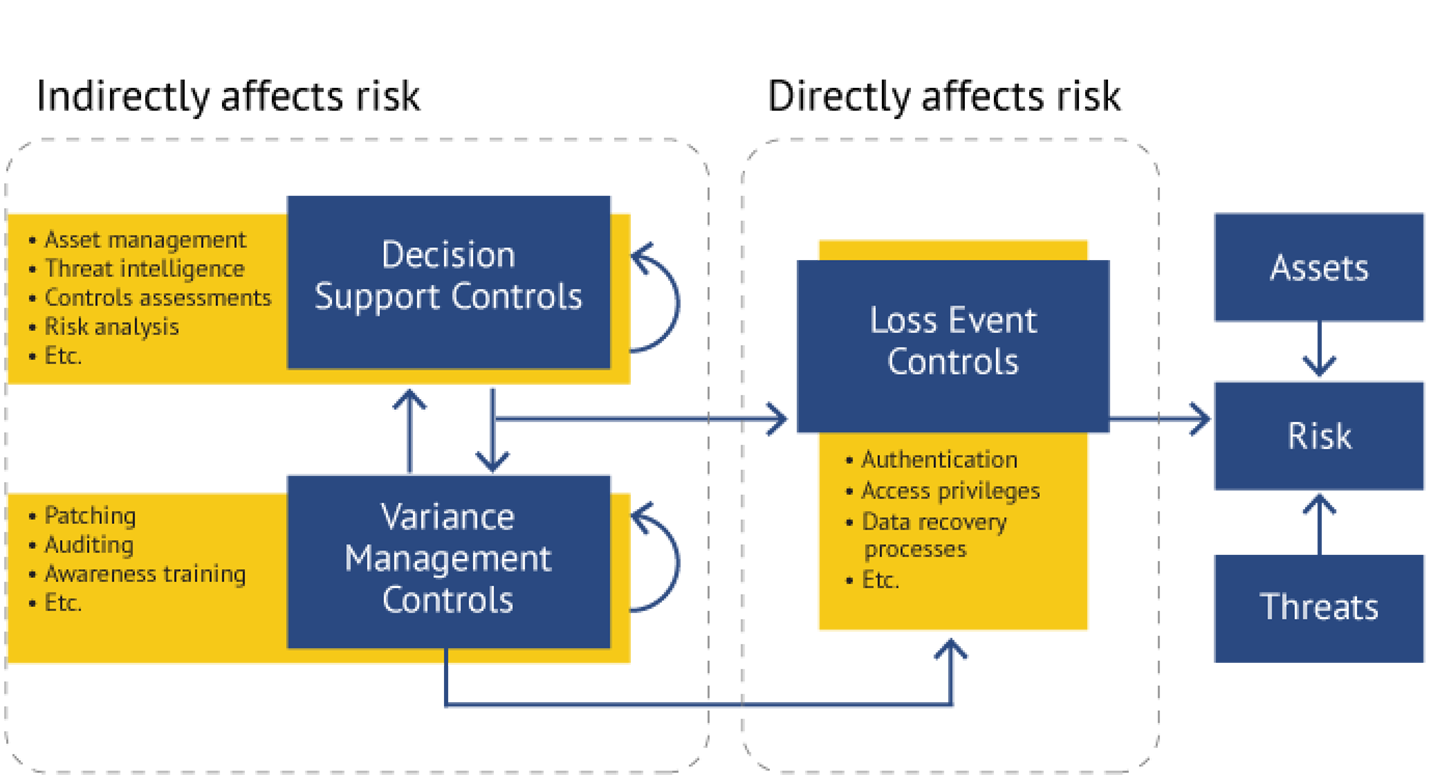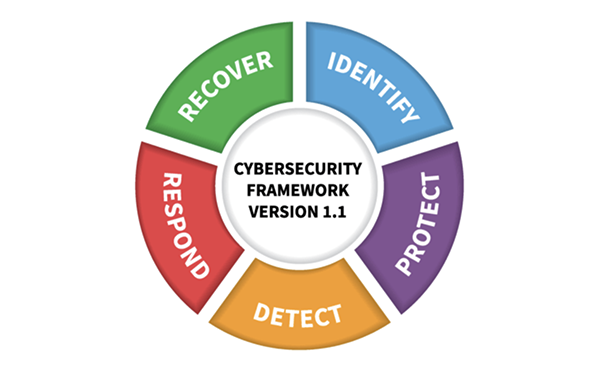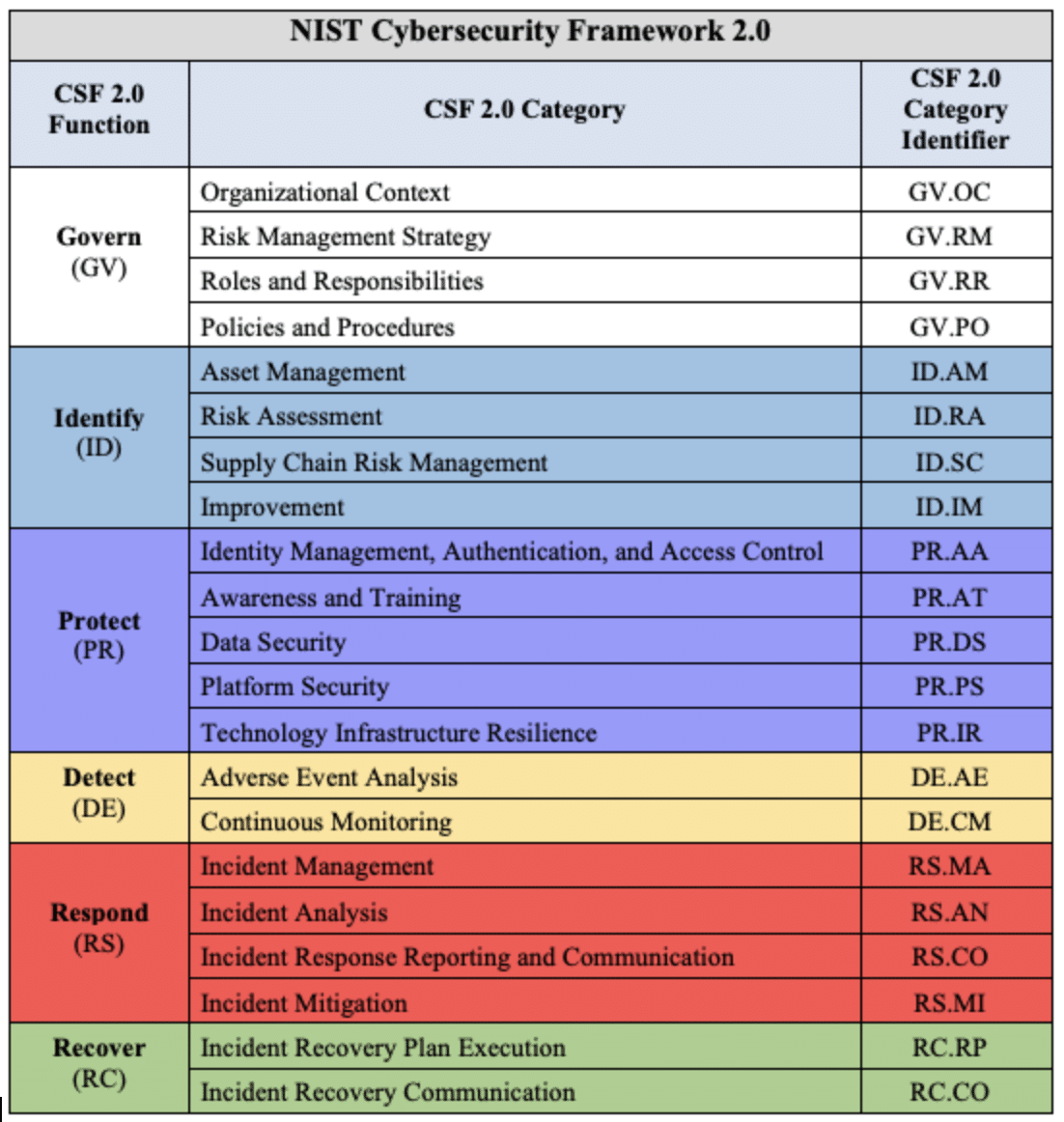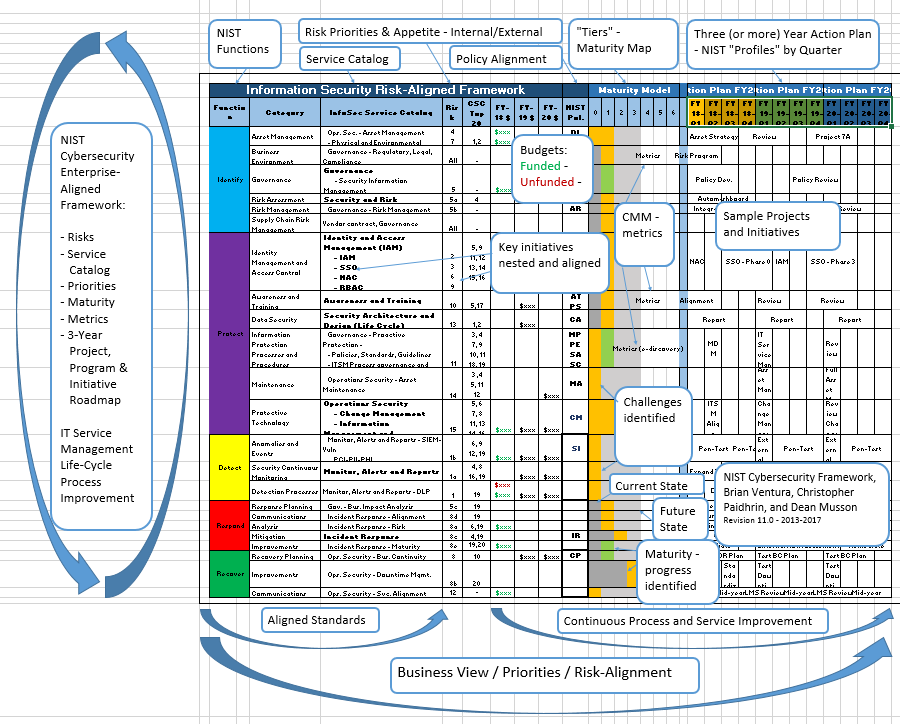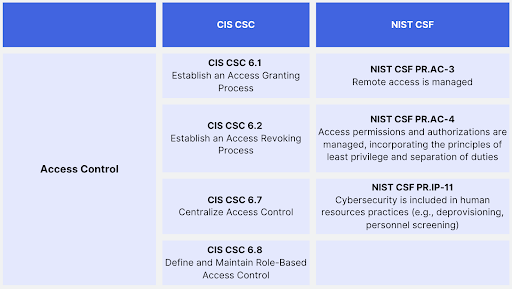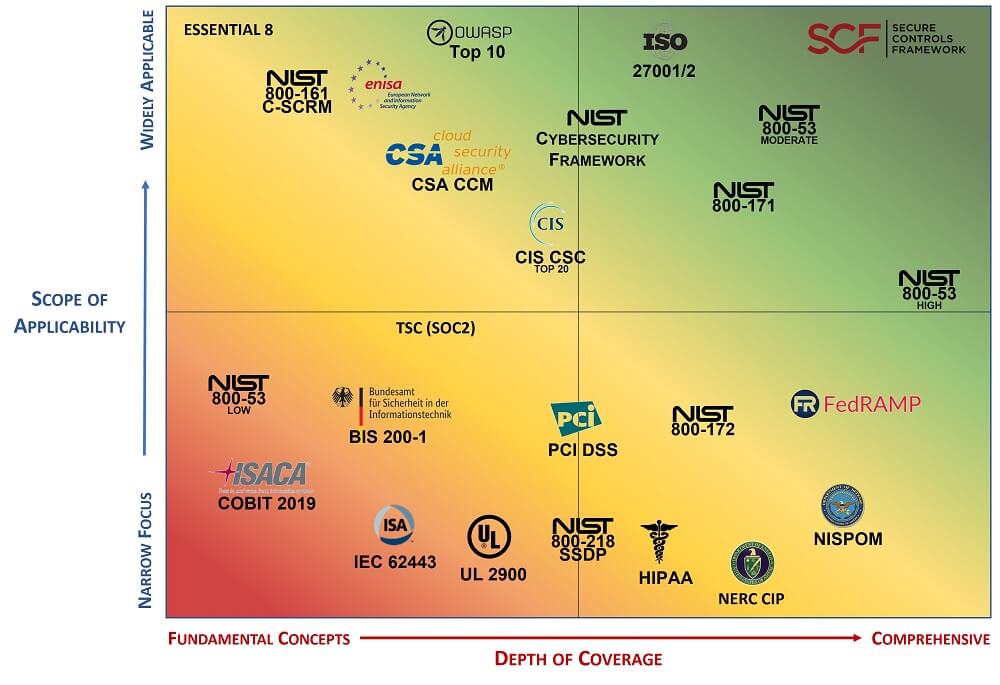
Start Here - Governance Risk & Compliance (GRC) - NIST 800-53 vs ISO 27002 vs NIST CSF vs SCF - ComplianceForge
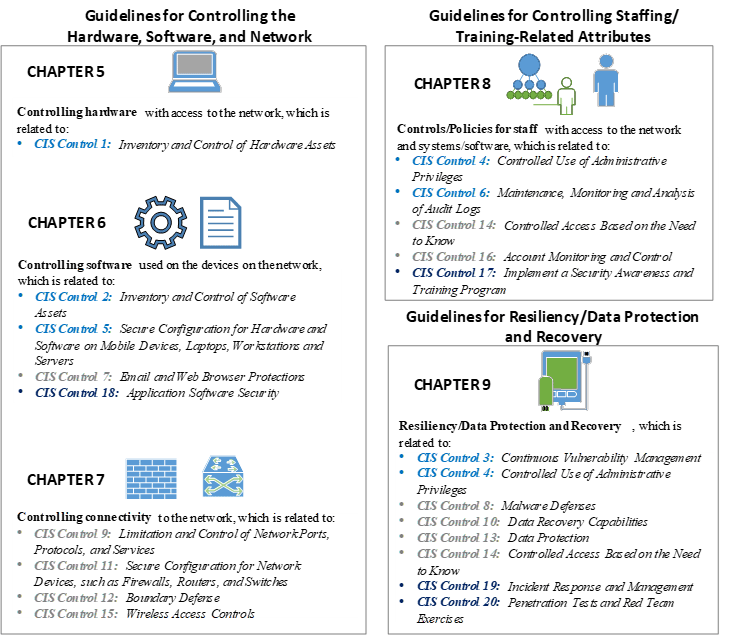
Transportation Management Center Information Technology Security - Chapter 4. Technical Guidelines and Recommended Practices - FHWA Office of Operations
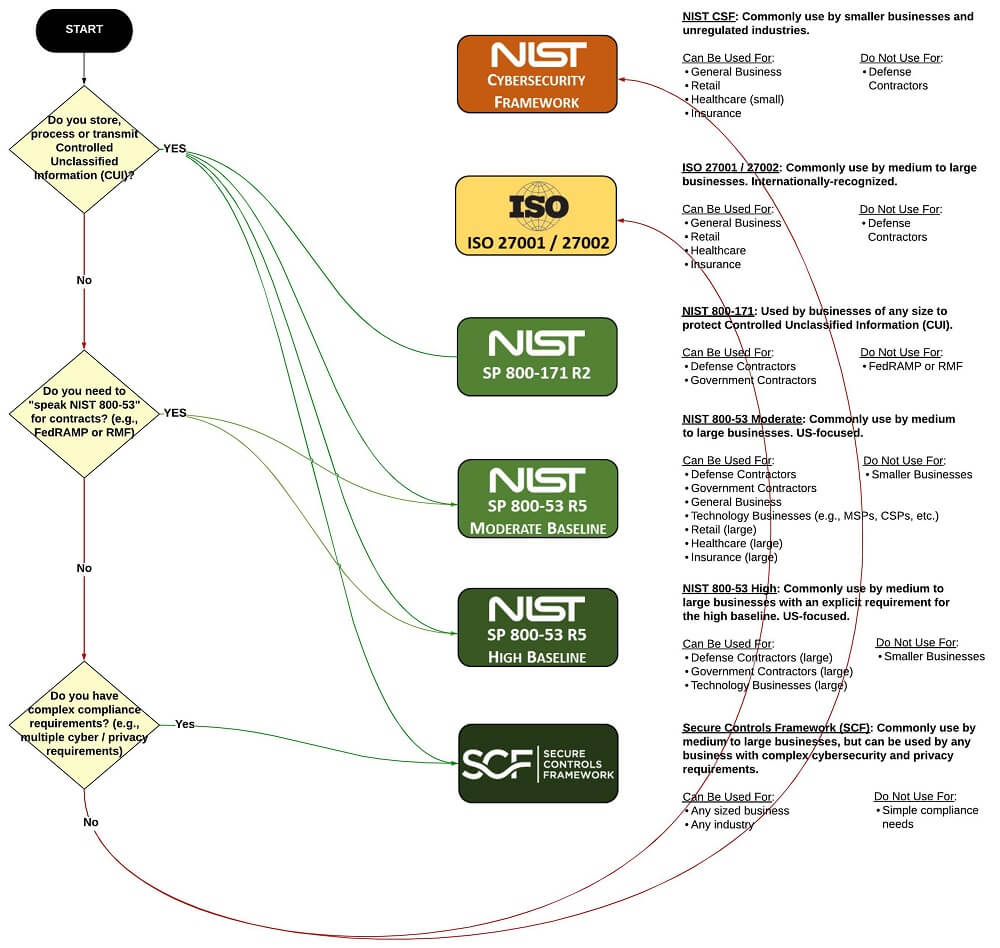
Start Here - Governance Risk & Compliance (GRC) - NIST 800-53 vs ISO 27002 vs NIST CSF vs SCF - ComplianceForge