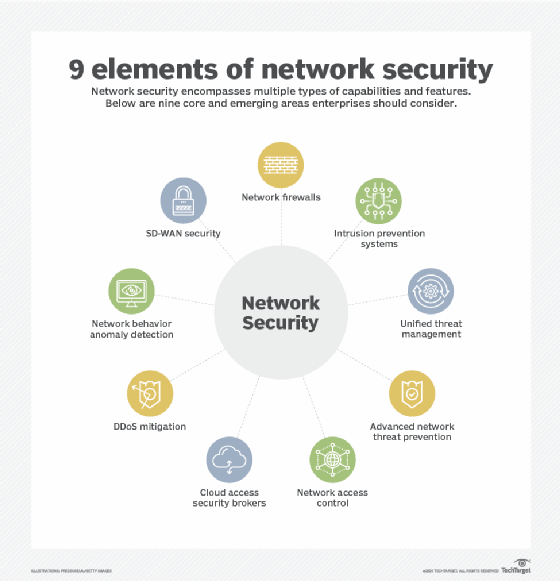
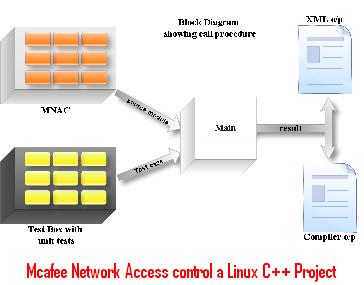
Tcpip WiFi Linux Access Control Network Office Punch Card Smart Attendance Machine Biometric Finger Print Time Clock with Linux Sdk - China RFID Access Control, Door Access Control | Made-in-China.com

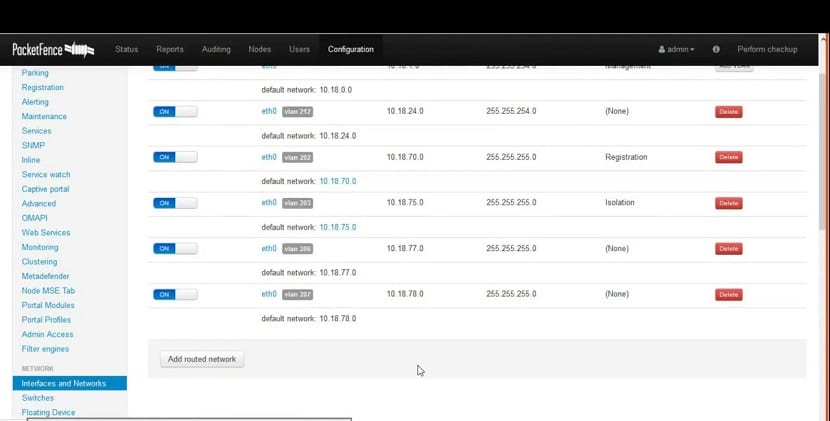
TCP/IP RS45 Linux Web Based Network Door Access Control System with Metal Case - China Access Control, Door Access Control | Made-in-China.com

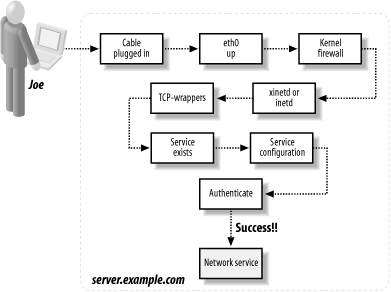
TCP/IP RS45 Linux Web Based Network Door Access Control System with Metal Case - China Access Control, Door Access Control | Made-in-China.com

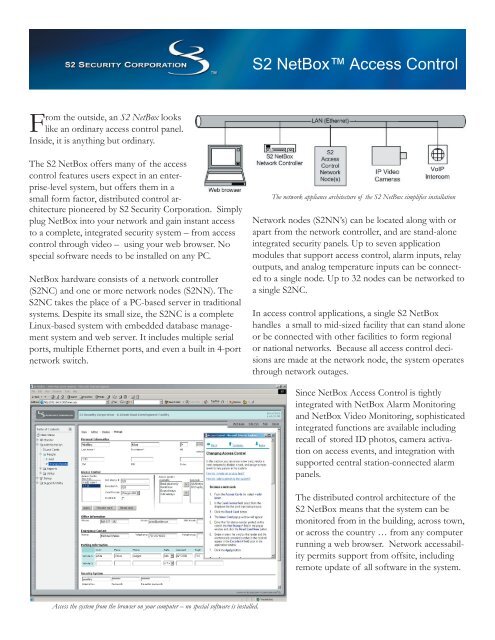
TCP/IP RS45 Linux Web Based Network Door Access Control System with Metal Case - China Access Control, Door Access Control | Made-in-China.com