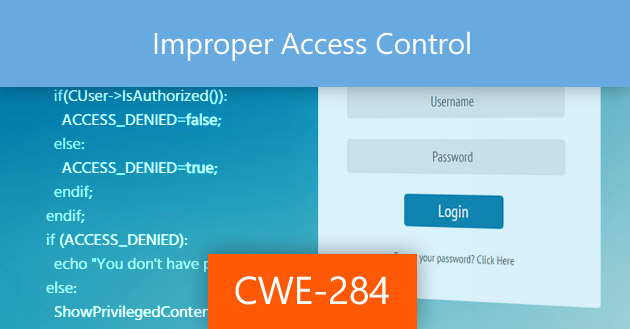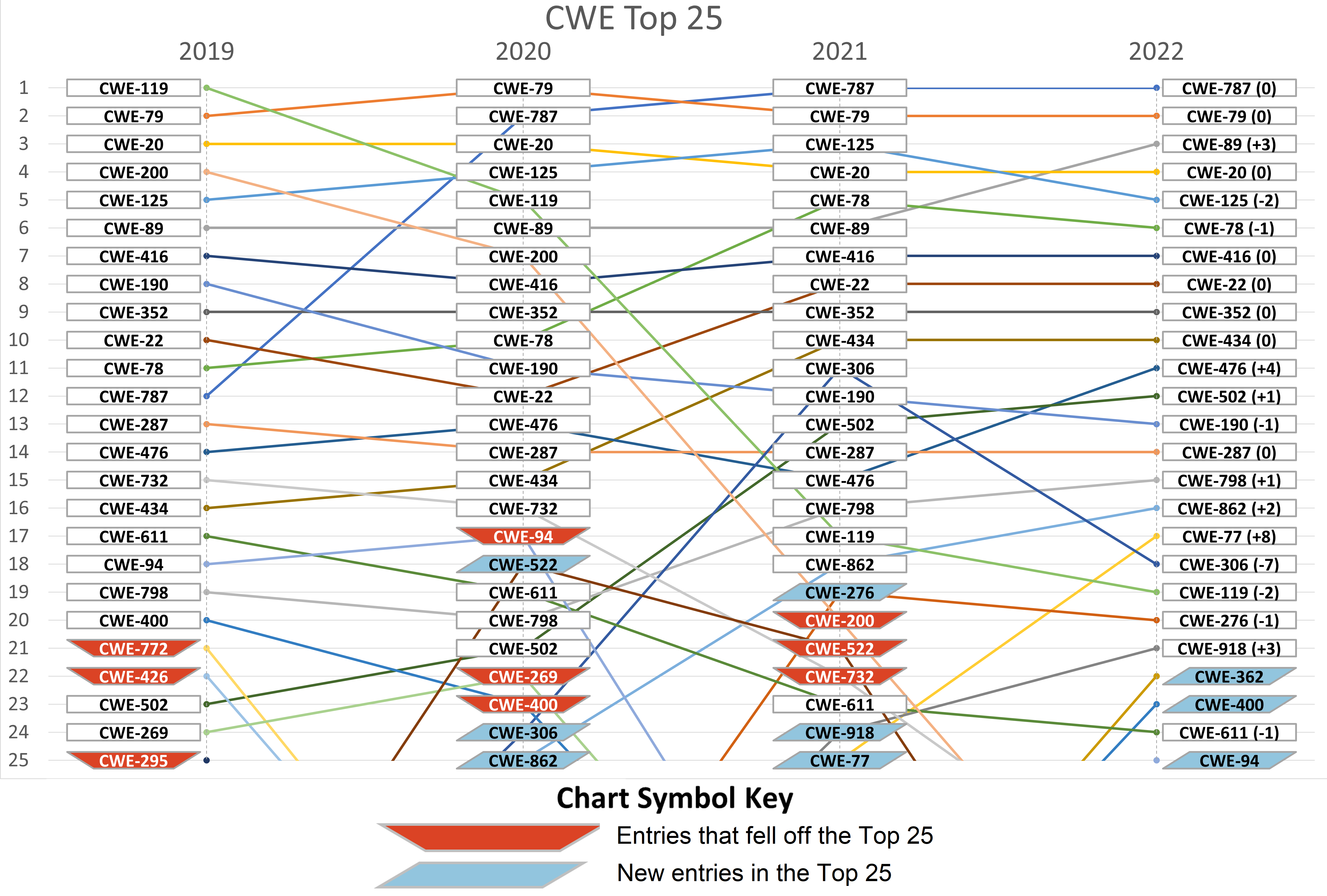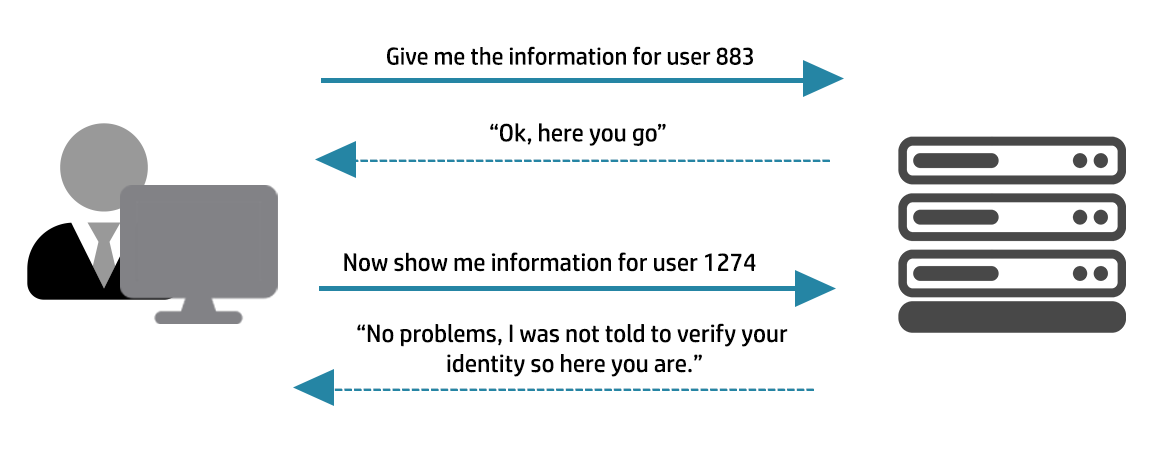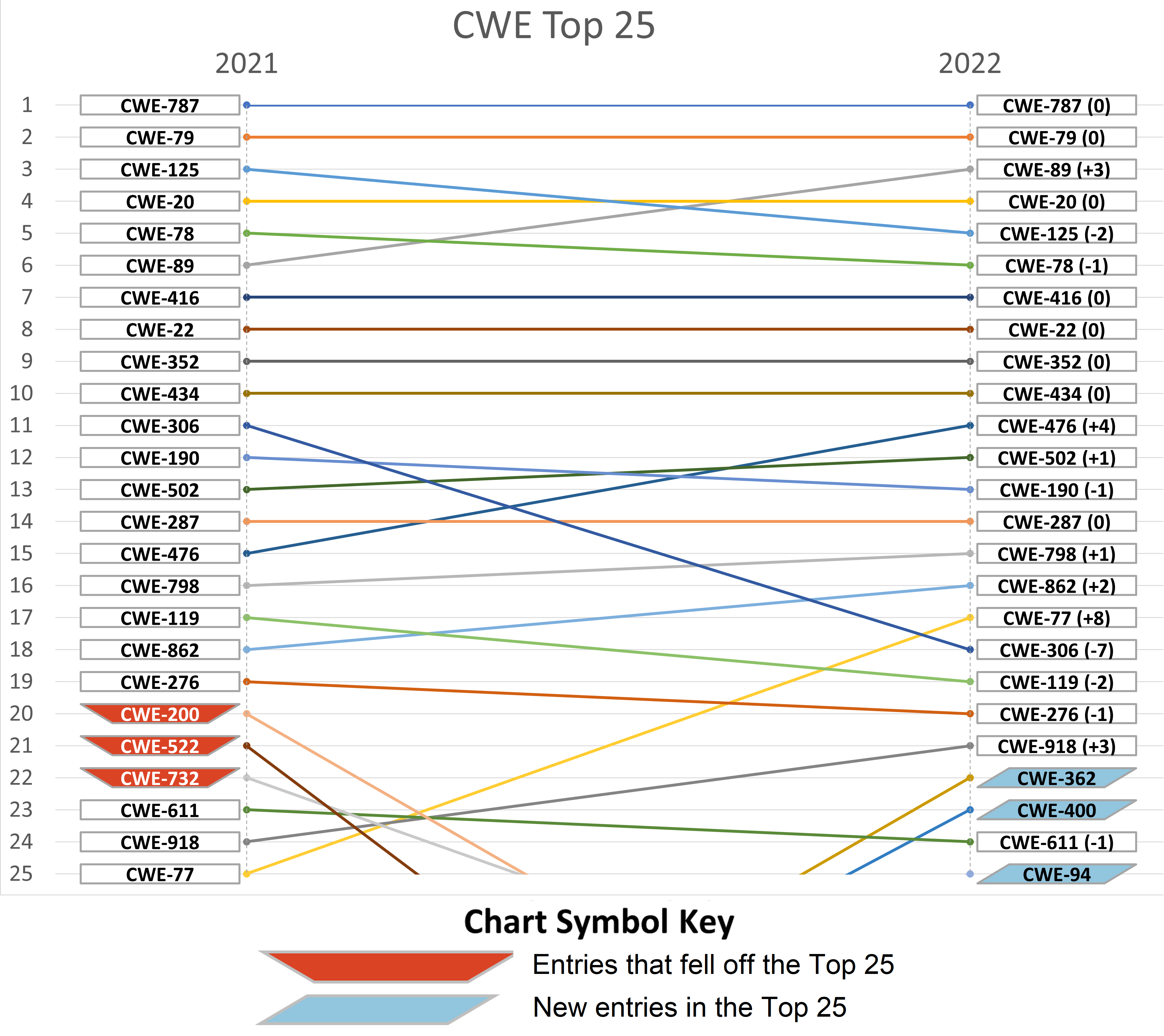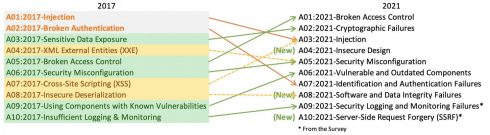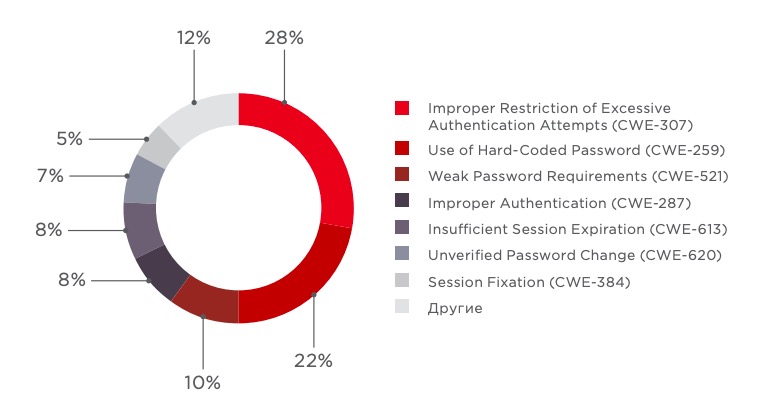
API security: Broken access controls, injection attacks plague the enterprise security landscape in 2022 | The Daily Swig

A quantitative security evaluation and analysis model for web applications based on OWASP application security verification standard - ScienceDirect
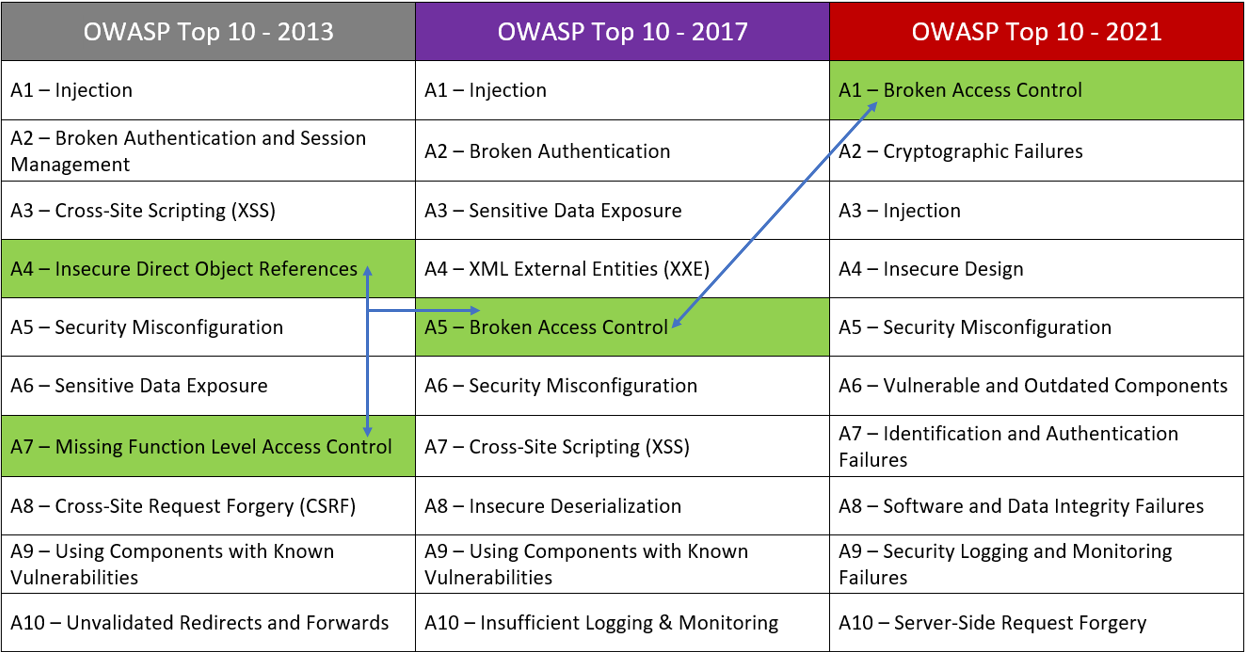
Rise of Broken Access Control. Why authorization flaws are trendy and… | by Rafin Rahman Chy | Nov, 2023 | InfoSec Write-ups

Manas on X: "Wanted to post this earlier. Always look for every possible way to find a broken access control, either endpoints or functionalities. Found 3 IDORS here. Reporting was average. @SynackRedTeam