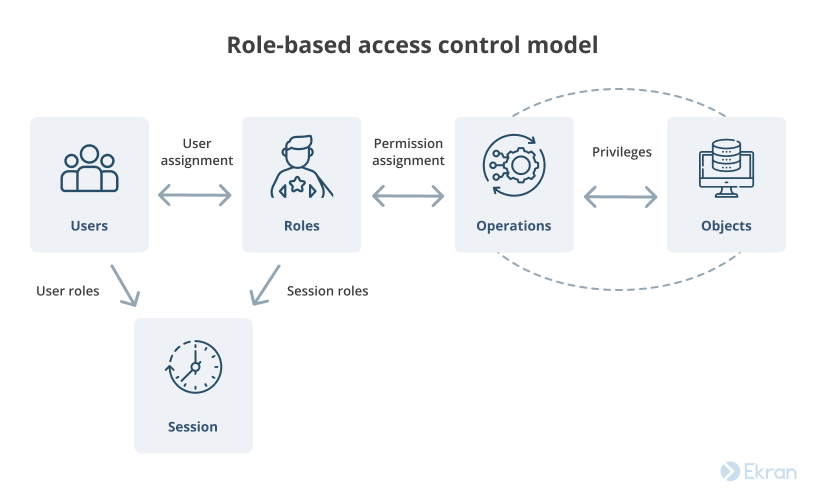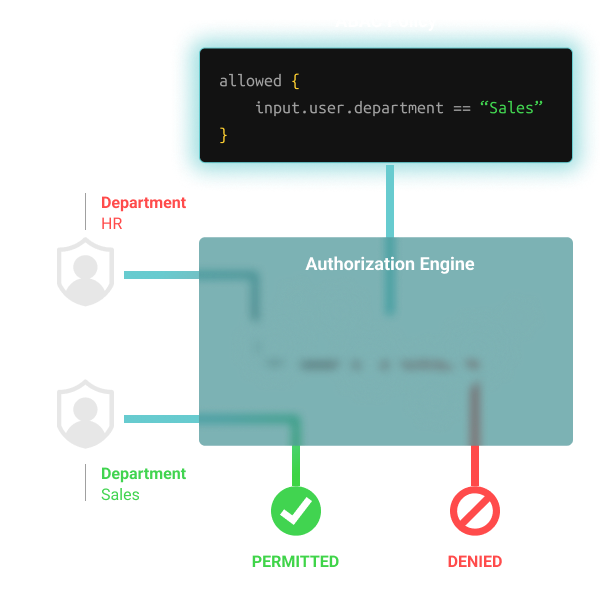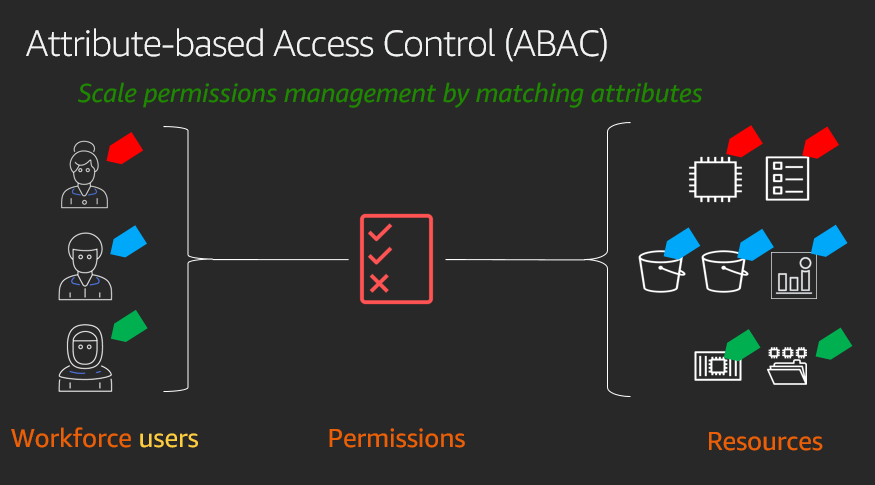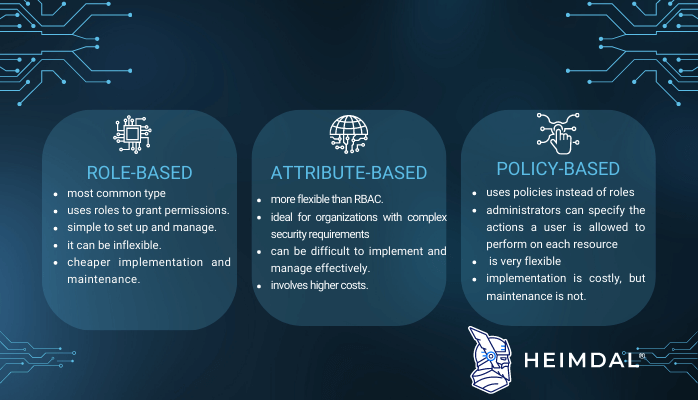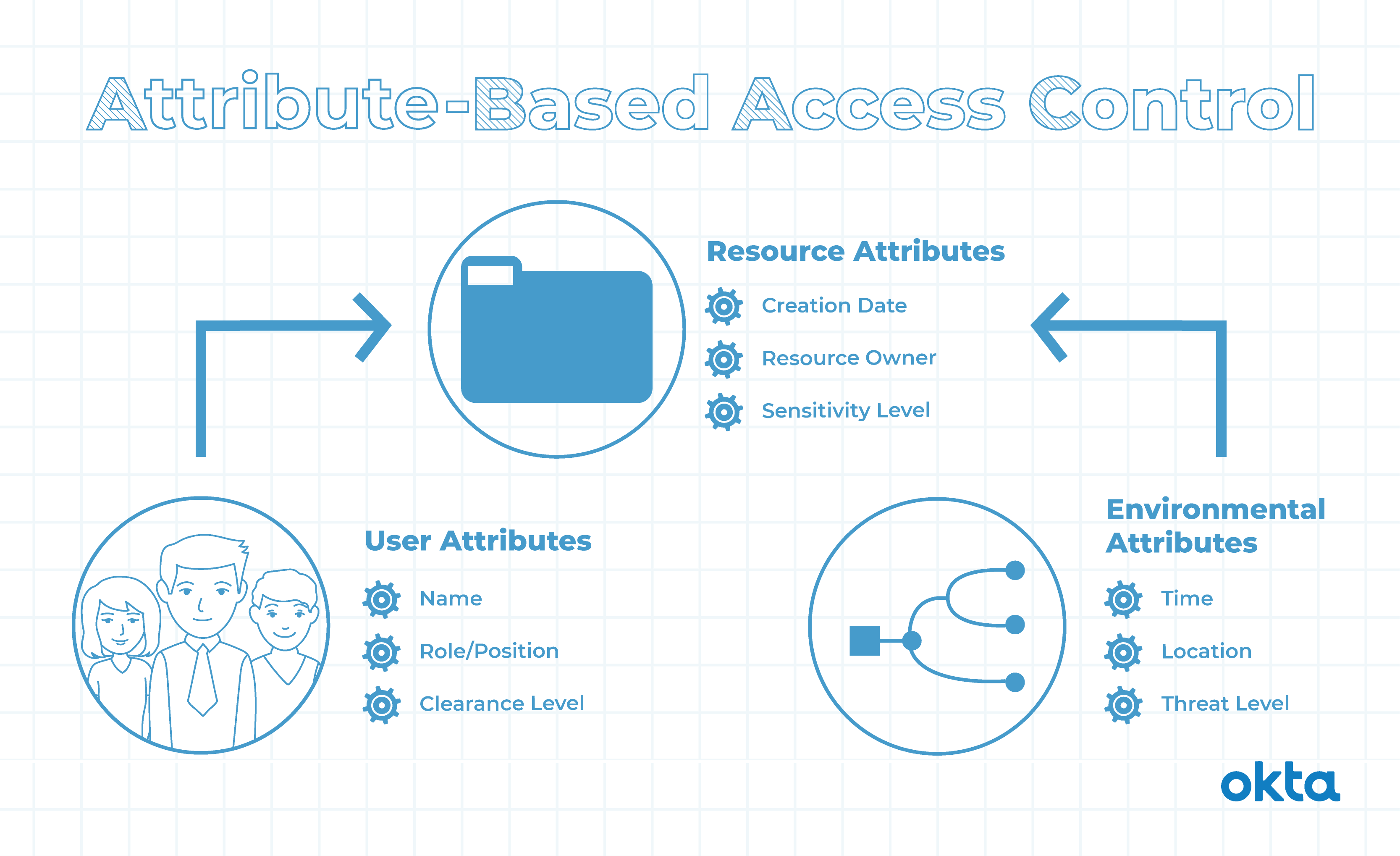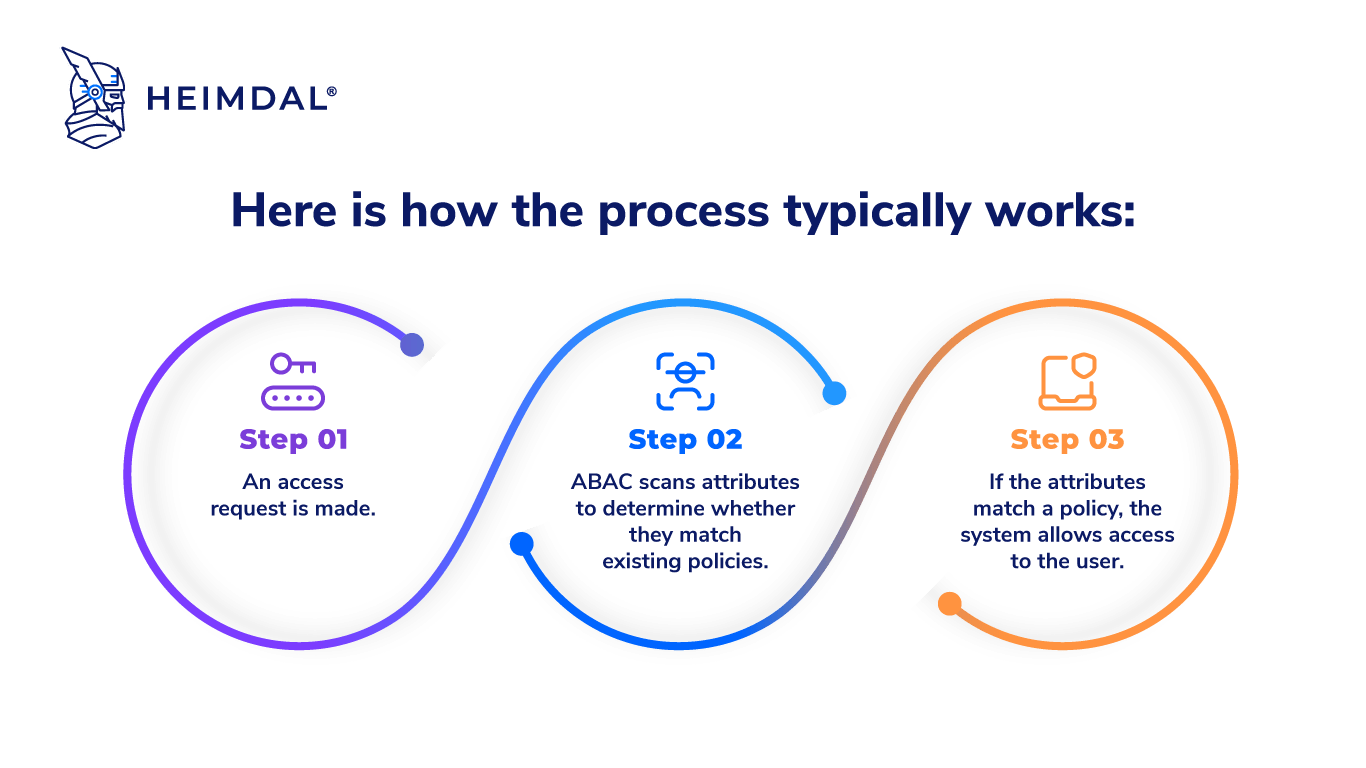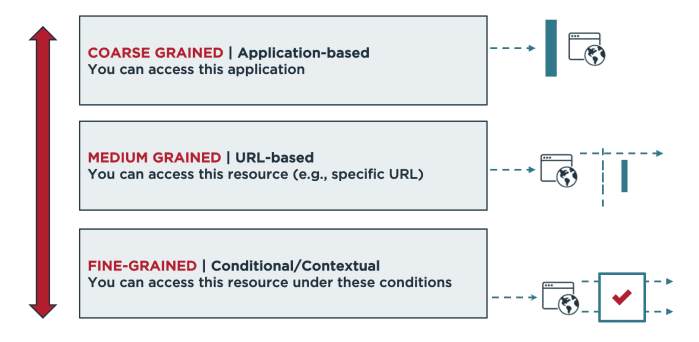
Role-based Access Control (RBAC) vs. Attribute-based Access Control (ABAC) : What's the Difference? | Ping Identity

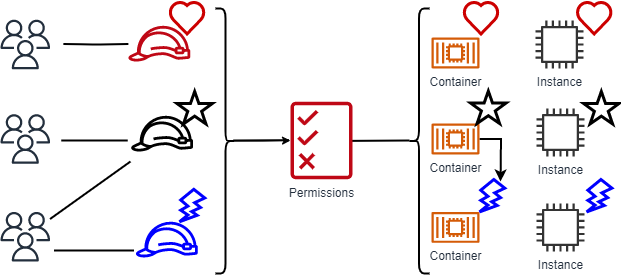
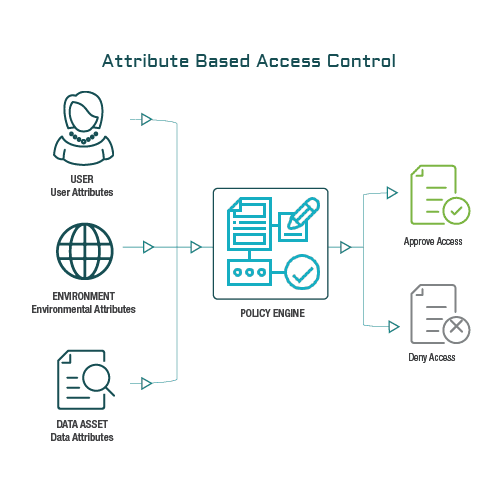
Figure 2 from Comparison of Attribute Based Access Control (ABAC) Model and Rule Based Access (RBAC) to Digital Evidence Storage (DES) | Semantic Scholar
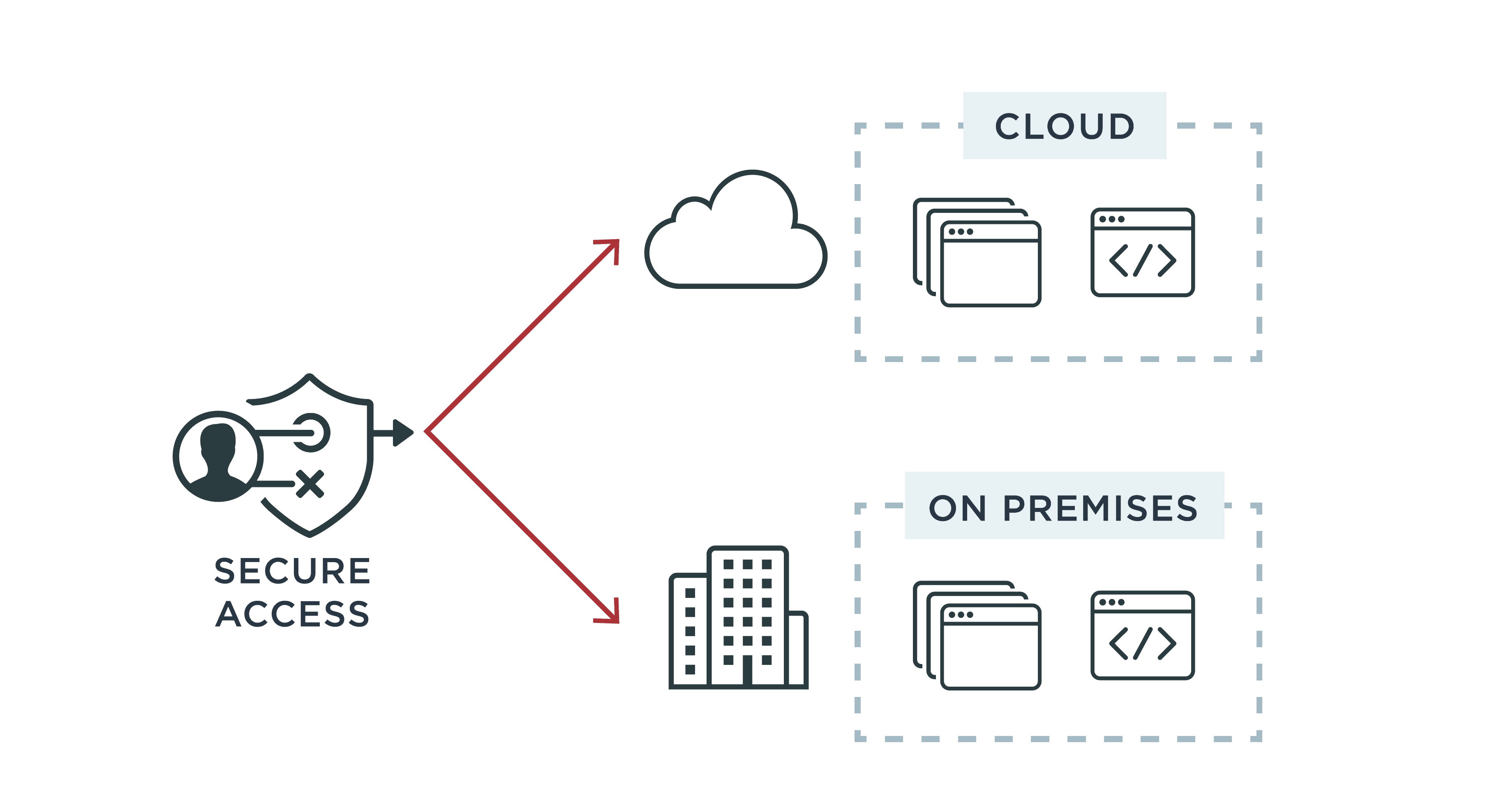
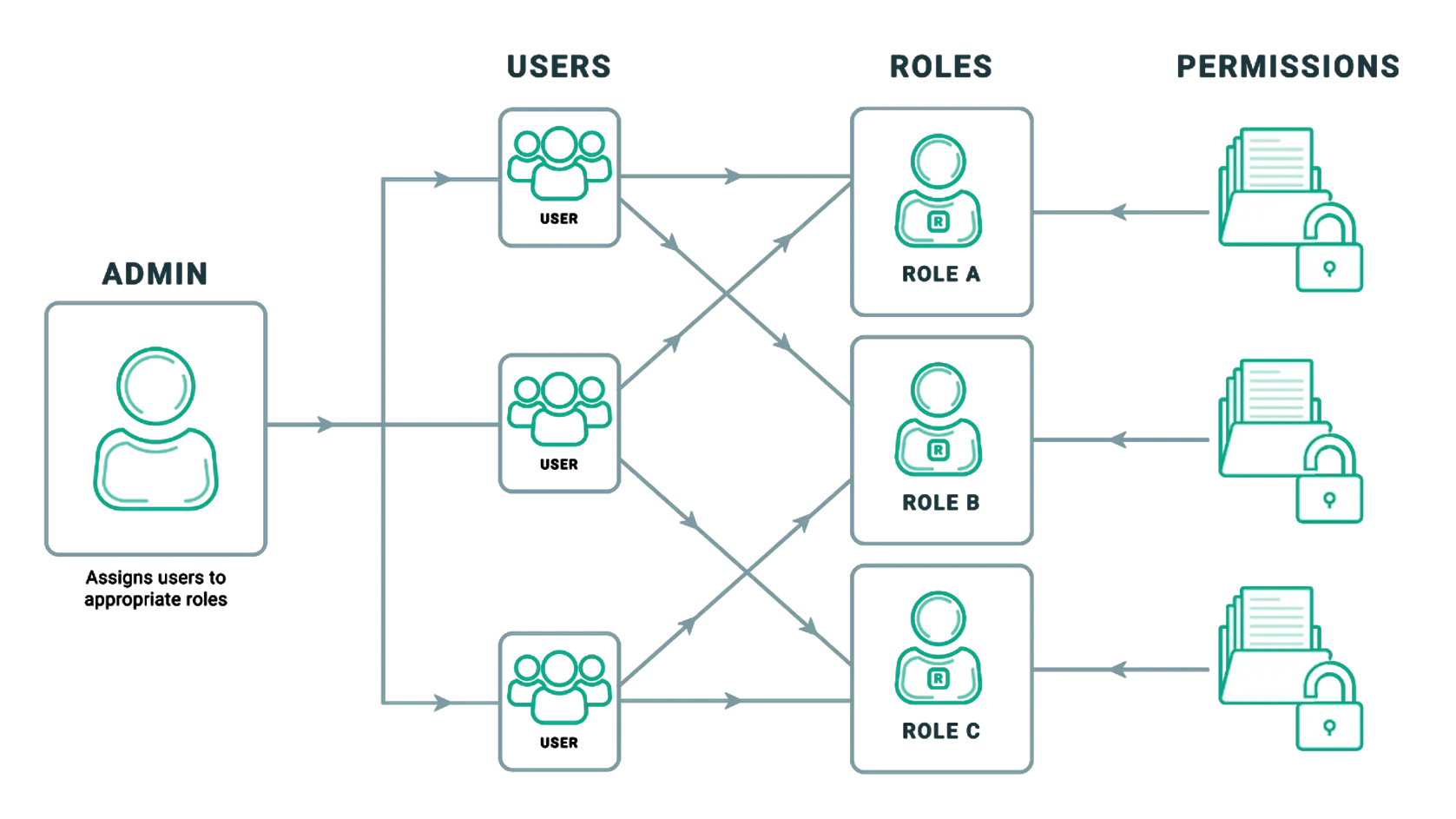
Role-based Access Control (RBAC) vs. Attribute-based Access Control (ABAC) : What's the Difference? | Ping Identity
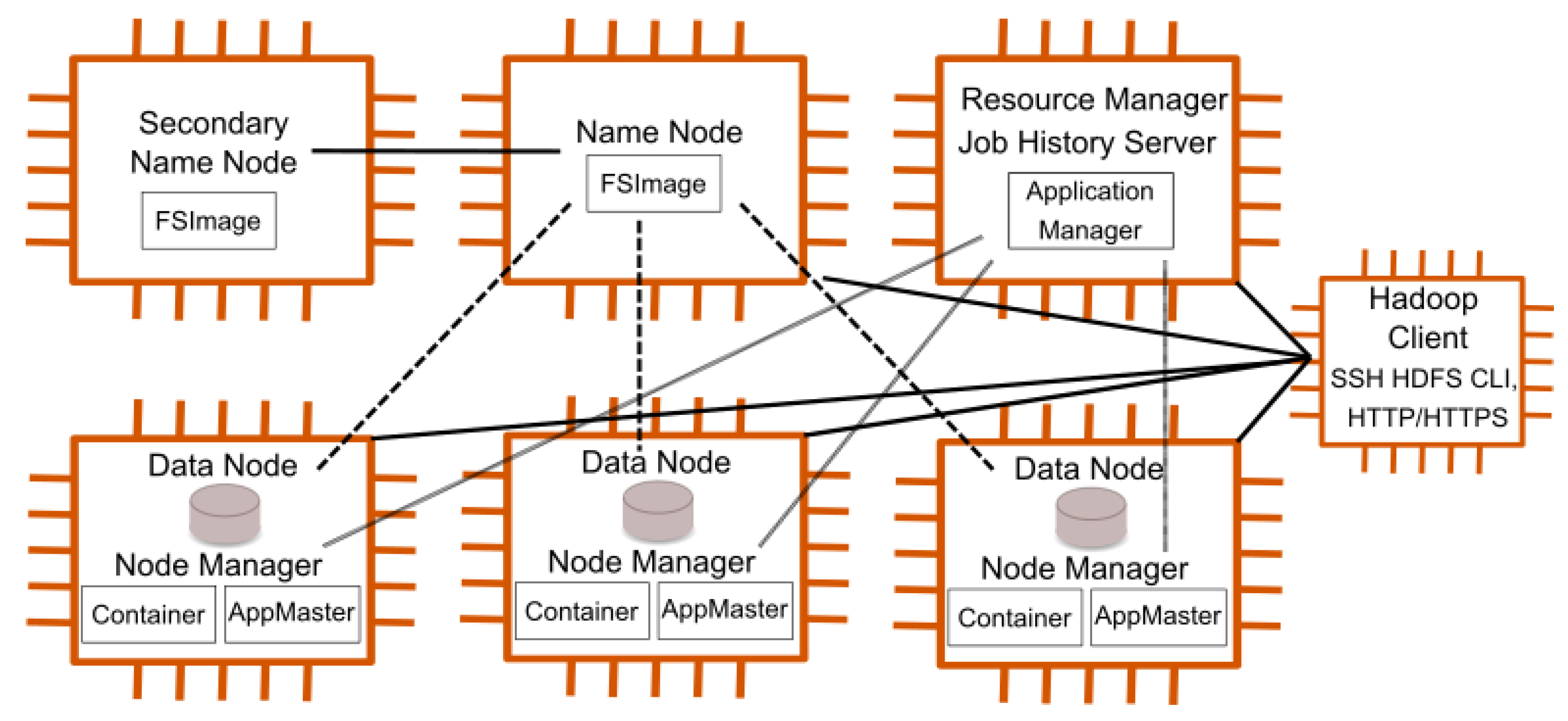
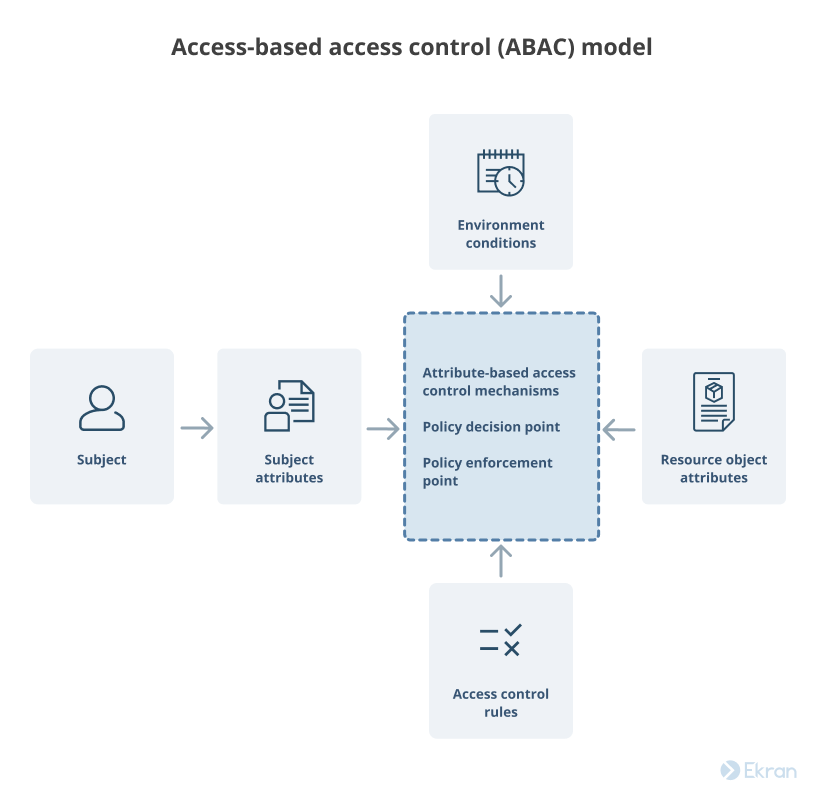
Applied Sciences | Free Full-Text | A Framework for Attribute-Based Access Control in Processing Big Data with Multiple Sensitivities